- 1. API with NestJS #1. Controllers, routing and the module structure
- 2. API with NestJS #2. Setting up a PostgreSQL database with TypeORM
- 3. API with NestJS #3. Authenticating users with bcrypt, Passport, JWT, and cookies
- 4. API with NestJS #4. Error handling and data validation
- 5. API with NestJS #5. Serializing the response with interceptors
- 6. API with NestJS #6. Looking into dependency injection and modules
- 7. API with NestJS #7. Creating relationships with Postgres and TypeORM
- 8. API with NestJS #8. Writing unit tests
- 9. API with NestJS #9. Testing services and controllers with integration tests
- 10. API with NestJS #10. Uploading public files to Amazon S3
- 11. API with NestJS #11. Managing private files with Amazon S3
- 12. API with NestJS #12. Introduction to Elasticsearch
- 13. API with NestJS #13. Implementing refresh tokens using JWT
- 14. API with NestJS #14. Improving performance of our Postgres database with indexes
- 15. API with NestJS #15. Defining transactions with PostgreSQL and TypeORM
- 16. API with NestJS #16. Using the array data type with PostgreSQL and TypeORM
- 17. API with NestJS #17. Offset and keyset pagination with PostgreSQL and TypeORM
- 18. API with NestJS #18. Exploring the idea of microservices
- 19. API with NestJS #19. Using RabbitMQ to communicate with microservices
- 20. API with NestJS #20. Communicating with microservices using the gRPC framework
- 21. API with NestJS #21. An introduction to CQRS
- 22. API with NestJS #22. Storing JSON with PostgreSQL and TypeORM
- 23. API with NestJS #23. Implementing in-memory cache to increase the performance
- 24. API with NestJS #24. Cache with Redis. Running the app in a Node.js cluster
- 25. API with NestJS #25. Sending scheduled emails with cron and Nodemailer
- 26. API with NestJS #26. Real-time chat with WebSockets
- 27. API with NestJS #27. Introduction to GraphQL. Queries, mutations, and authentication
- 28. API with NestJS #28. Dealing in the N + 1 problem in GraphQL
- 29. API with NestJS #29. Real-time updates with GraphQL subscriptions
- 30. API with NestJS #30. Scalar types in GraphQL
- 31. API with NestJS #31. Two-factor authentication
- 32. API with NestJS #32. Introduction to Prisma with PostgreSQL
- 33. API with NestJS #33. Managing PostgreSQL relationships with Prisma
- 34. API with NestJS #34. Handling CPU-intensive tasks with queues
- 35. API with NestJS #35. Using server-side sessions instead of JSON Web Tokens
- 36. API with NestJS #36. Introduction to Stripe with React
- 37. API with NestJS #37. Using Stripe to save credit cards for future use
- 38. API with NestJS #38. Setting up recurring payments via subscriptions with Stripe
- 39. API with NestJS #39. Reacting to Stripe events with webhooks
- 40. API with NestJS #40. Confirming the email address
- 41. API with NestJS #41. Verifying phone numbers and sending SMS messages with Twilio
- 42. API with NestJS #42. Authenticating users with Google
- 43. API with NestJS #43. Introduction to MongoDB
- 44. API with NestJS #44. Implementing relationships with MongoDB
- 45. API with NestJS #45. Virtual properties with MongoDB and Mongoose
- 46. API with NestJS #46. Managing transactions with MongoDB and Mongoose
- 47. API with NestJS #47. Implementing pagination with MongoDB and Mongoose
- 48. API with NestJS #48. Definining indexes with MongoDB and Mongoose
- 49. API with NestJS #49. Updating with PUT and PATCH with MongoDB and Mongoose
- 50. API with NestJS #50. Introduction to logging with the built-in logger and TypeORM
- 51. API with NestJS #51. Health checks with Terminus and Datadog
- 52. API with NestJS #52. Generating documentation with Compodoc and JSDoc
- 53. API with NestJS #53. Implementing soft deletes with PostgreSQL and TypeORM
- 54. API with NestJS #54. Storing files inside a PostgreSQL database
- 55. API with NestJS #55. Uploading files to the server
- 56. API with NestJS #56. Authorization with roles and claims
- 57. API with NestJS #57. Composing classes with the mixin pattern
- 58. API with NestJS #58. Using ETag to implement cache and save bandwidth
- 59. API with NestJS #59. Introduction to a monorepo with Lerna and Yarn workspaces
- 60. API with NestJS #60. The OpenAPI specification and Swagger
- 61. API with NestJS #61. Dealing with circular dependencies
- 62. API with NestJS #62. Introduction to MikroORM with PostgreSQL
- 63. API with NestJS #63. Relationships with PostgreSQL and MikroORM
- 64. API with NestJS #64. Transactions with PostgreSQL and MikroORM
- 65. API with NestJS #65. Implementing soft deletes using MikroORM and filters
- 66. API with NestJS #66. Improving PostgreSQL performance with indexes using MikroORM
- 67. API with NestJS #67. Migrating to TypeORM 0.3
- 68. API with NestJS #68. Interacting with the application through REPL
- 69. API with NestJS #69. Database migrations with TypeORM
- 70. API with NestJS #70. Defining dynamic modules
- 71. API with NestJS #71. Introduction to feature flags
- 72. API with NestJS #72. Working with PostgreSQL using raw SQL queries
- 73. API with NestJS #73. One-to-one relationships with raw SQL queries
- 74. API with NestJS #74. Designing many-to-one relationships using raw SQL queries
- 75. API with NestJS #75. Many-to-many relationships using raw SQL queries
- 76. API with NestJS #76. Working with transactions using raw SQL queries
- 77. API with NestJS #77. Offset and keyset pagination with raw SQL queries
- 78. API with NestJS #78. Generating statistics using aggregate functions in raw SQL
- 79. API with NestJS #79. Implementing searching with pattern matching and raw SQL
- 80. API with NestJS #80. Updating entities with PUT and PATCH using raw SQL queries
- 81. API with NestJS #81. Soft deletes with raw SQL queries
- 82. API with NestJS #82. Introduction to indexes with raw SQL queries
- 83. API with NestJS #83. Text search with tsvector and raw SQL
- 84. API with NestJS #84. Implementing filtering using subqueries with raw SQL
- 85. API with NestJS #85. Defining constraints with raw SQL
- 86. API with NestJS #86. Logging with the built-in logger when using raw SQL
- 87. API with NestJS #87. Writing unit tests in a project with raw SQL
- 88. API with NestJS #88. Testing a project with raw SQL using integration tests
- 89. API with NestJS #89. Replacing Express with Fastify
- 90. API with NestJS #90. Using various types of SQL joins
- 91. API with NestJS #91. Dockerizing a NestJS API with Docker Compose
- 92. API with NestJS #92. Increasing the developer experience with Docker Compose
- 93. API with NestJS #93. Deploying a NestJS app with Amazon ECS and RDS
- 94. API with NestJS #94. Deploying multiple instances on AWS with a load balancer
- 95. API with NestJS #95. CI/CD with Amazon ECS and GitHub Actions
- 96. API with NestJS #96. Running unit tests with CI/CD and GitHub Actions
- 97. API with NestJS #97. Introduction to managing logs with Amazon CloudWatch
- 98. API with NestJS #98. Health checks with Terminus and Amazon ECS
- 99. API with NestJS #99. Scaling the number of application instances with Amazon ECS
- 100. API with NestJS #100. The HTTPS protocol with Route 53 and AWS Certificate Manager
- 101. API with NestJS #101. Managing sensitive data using the AWS Secrets Manager
- 102. API with NestJS #102. Writing unit tests with Prisma
- 103. API with NestJS #103. Integration tests with Prisma
- 104. API with NestJS #104. Writing transactions with Prisma
- 105. API with NestJS #105. Implementing soft deletes with Prisma and middleware
- 106. API with NestJS #106. Improving performance through indexes with Prisma
- 107. API with NestJS #107. Offset and keyset pagination with Prisma
- 108. API with NestJS #108. Date and time with Prisma and PostgreSQL
- 109. API with NestJS #109. Arrays with PostgreSQL and Prisma
- 110. API with NestJS #110. Managing JSON data with PostgreSQL and Prisma
- 111. API with NestJS #111. Constraints with PostgreSQL and Prisma
- 112. API with NestJS #112. Serializing the response with Prisma
- 113. API with NestJS #113. Logging with Prisma
- 114. API with NestJS #114. Modifying data using PUT and PATCH methods with Prisma
- 115. API with NestJS #115. Database migrations with Prisma
- 116. API with NestJS #116. REST API versioning
- 117. API with NestJS #117. CORS – Cross-Origin Resource Sharing
- 118. API with NestJS #118. Uploading and streaming videos
- 119. API with NestJS #119. Type-safe SQL queries with Kysely and PostgreSQL
- 120. API with NestJS #120. One-to-one relationships with the Kysely query builder
- 121. API with NestJS #121. Many-to-one relationships with PostgreSQL and Kysely
In the previous article, we learned how to use the Elastic Container Service (ECS) to deploy a single instance of our application. This time, we take a step further and deploy multiple instances with a load balancer distributing the traffic.
Our application might perform as expected on most days. However, there are times, such as Black Friday, when we might expect increased traffic. One way of dealing with that would be vertically scaling our resources by adding faster CPUs or memory to an existing server. Unfortunately, this is not easy to do without downtime.
Instead, we can scale horizontally by running additional instances of our application and splitting the workload between them. It’s easier to accomplish without downtime. Also, if one of our instances malfunctions, we can distribute the traffic to the other instances.
This article is a direct continuation of API with NestJS #93. Deploying a NestJS app with Amazon ECS and RDS
Creating the security groups
Security groups control the traffic allowed to reach and leave particular resources. In the previous article, we modified the default security groups to allow the instance of our application to accept incoming traffic. This time, we will create two security groups from scratch.
Security group for the load balancer
When we use a load balancer, the clients requesting our API don’t connect directly with an instance of our application. Instead, they request the load balancer. Its role is to forward the request to one of the application instances.
We need to define appropriate security group rules to allow the load balancer to accept incoming traffic. To create a new security group, we need to go to the EC2 panel and click on the “Security Groups” option on the left sidebar under the “Network & Security” category.
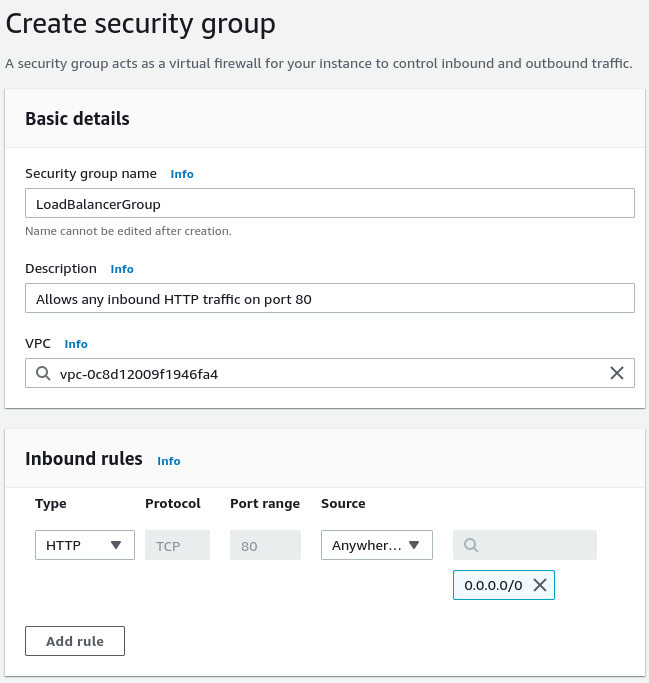
Above, the crucial part is adding an inbound rule that allows HTTP traffic on port 80 from the outside world.
Security group for the EC2 containers
Users send requests to our load balancer. Then, we expect the load balancer to forward the requests to our application running in the EC2 instances. For it to work, we need to allow the load balancer to communicate with our application explicitly. For that, let’s create a separate security group.
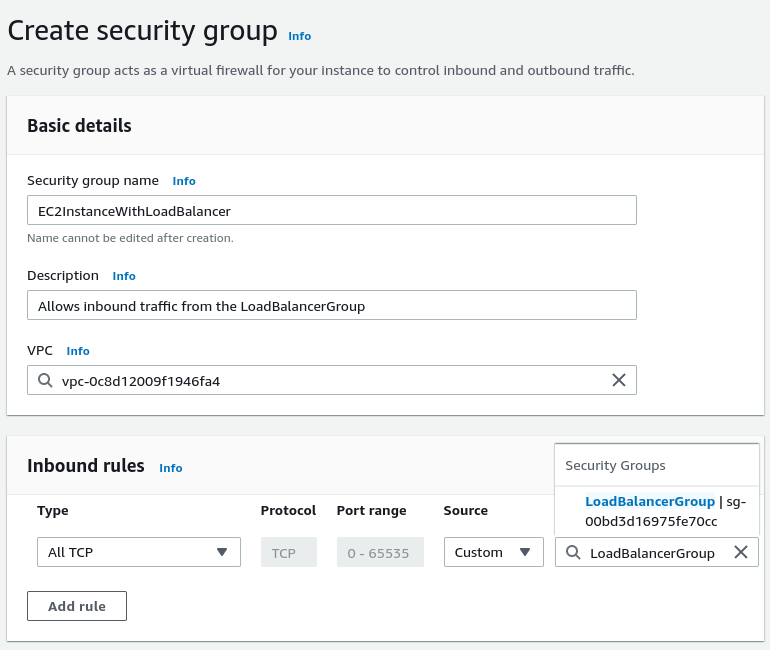
The crucial part of the above configuration is allowing the incoming traffic from the load balancer. We do that by selecting the security group we created before.
Preparing the ECS cluster
To perform the next steps, we need to have the ECS cluster. Let’s create it.
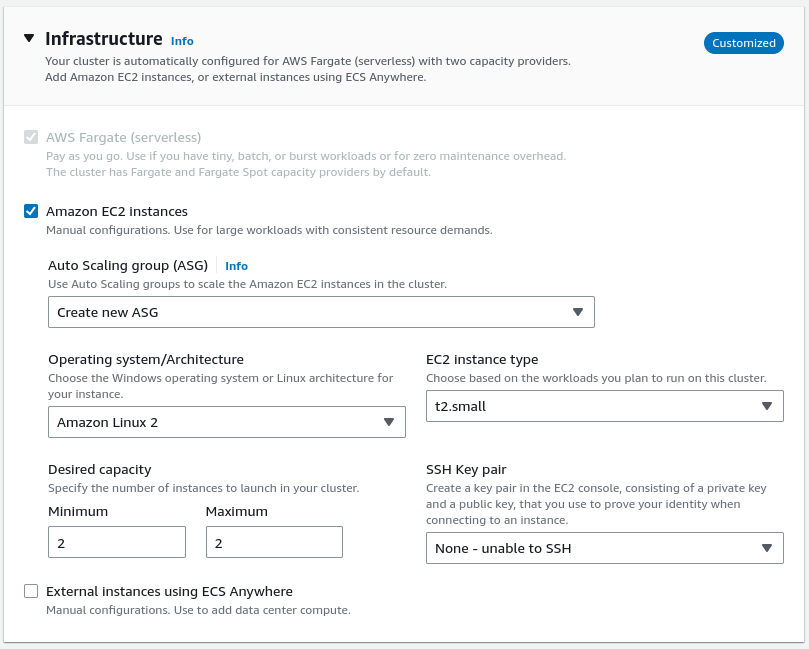
The crucial part of its configuration is specifying the number of instances bigger than one. To keep it simple, let’s use two instances.
Creating the task definition
Our ECS cluster can run various tasks. To do that, we need to create the task definition. It is very similar to the one we created in the previous article.
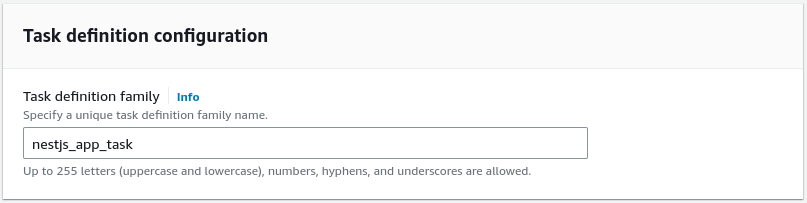
We again configure our task definition to use the URI of the Docker image we pushed to the Elastic Container Repository.
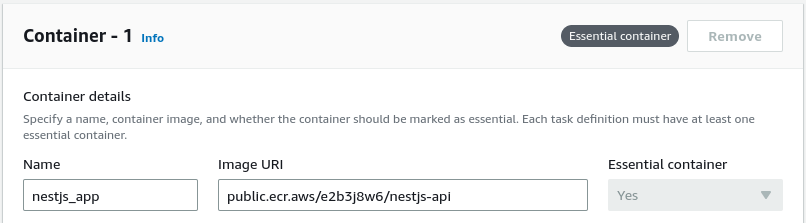
One more time, we expose port 3000, which our NestJS application uses.
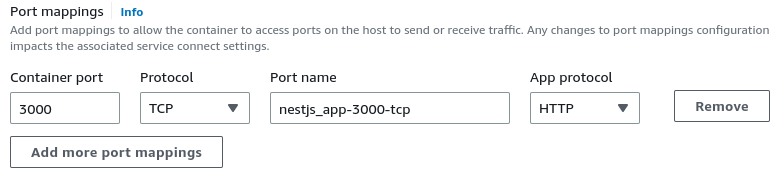
In the previous part of this series, we configured our task definition to use static host port mapping. However, the Application Load Balancer that we want to use with multiple instances of our application uses dynamic port mapping. Because of that, we won’t modify our task definition to set up the static mapping.
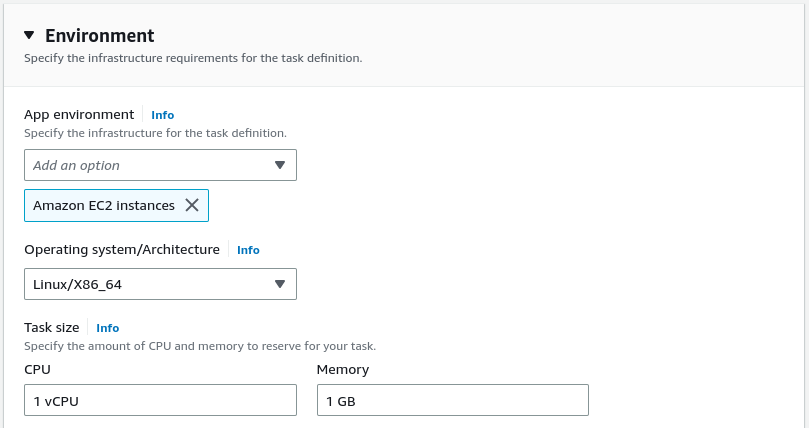
We also need to provide the environment variables our Docker image needs.
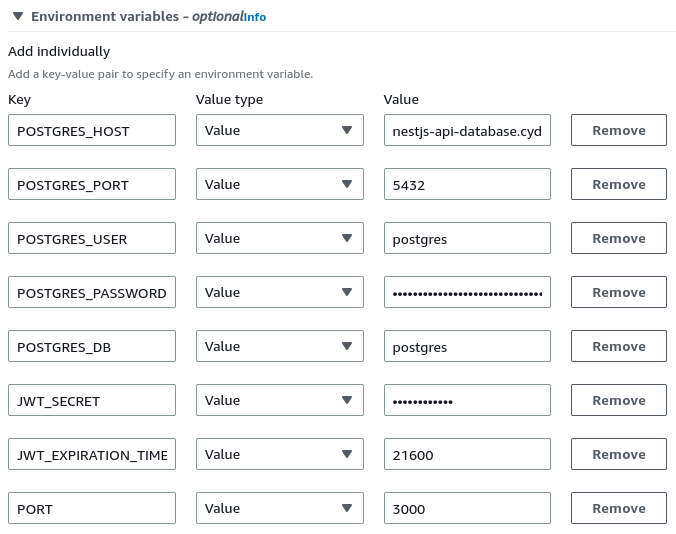
The part we need to configure is the environment.
Running multiple instances
Configuring the ECS cluster and the task definition is not that different from when we were using just one instance of our app. However, running the tasks is a bit different.
We need to open our new cluster and create a service that can run multiple tasks. We need to click on the “Create” button to do that.
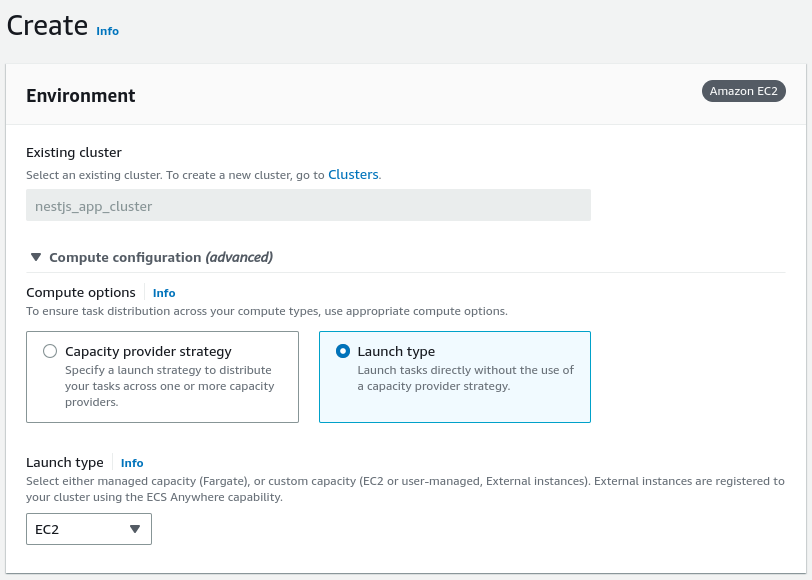
Since we want to use EC2 instances with our cluster, we must select the appropriate launch type.
We also need to choose the correct application type. By selecting “Service”, we can launch a group of tasks that can be distributed across our ECS cluster.
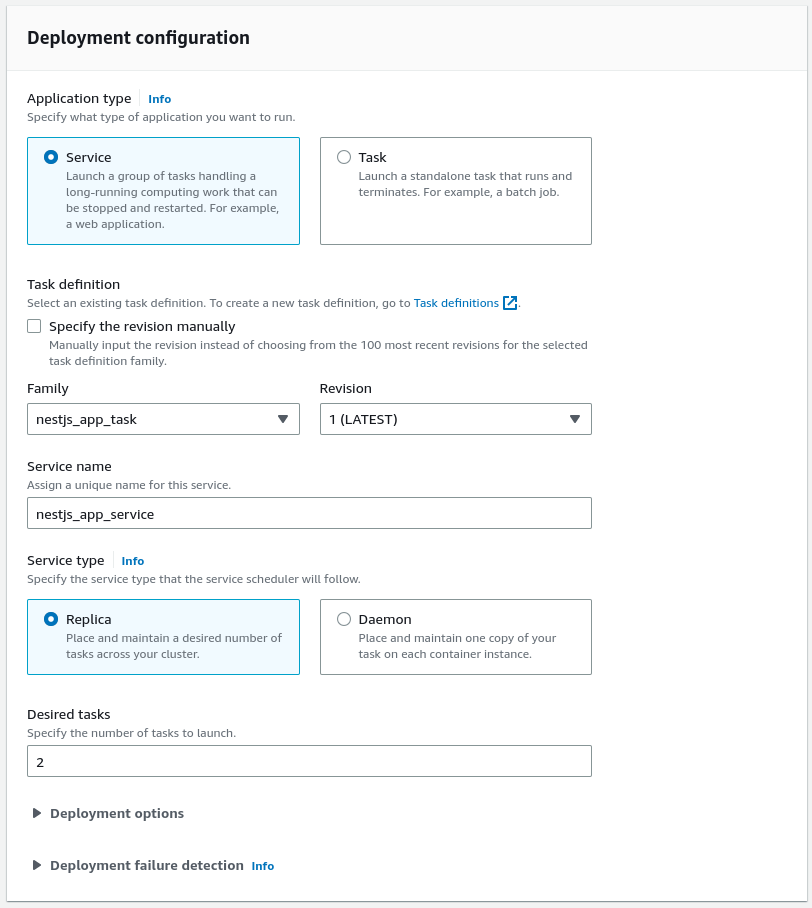
Choosing the Daemon service type would mean deploying exactly one task on each active container in our ECS clsuter. Instead, we can use Replica to allow AWS to distribute the the tasks across the cluster.
The part crucial to us in this article is configuring the Load balancing. This is where we have the chance to create a new load balancer. One of the most essential parts of its configuration is the target group.
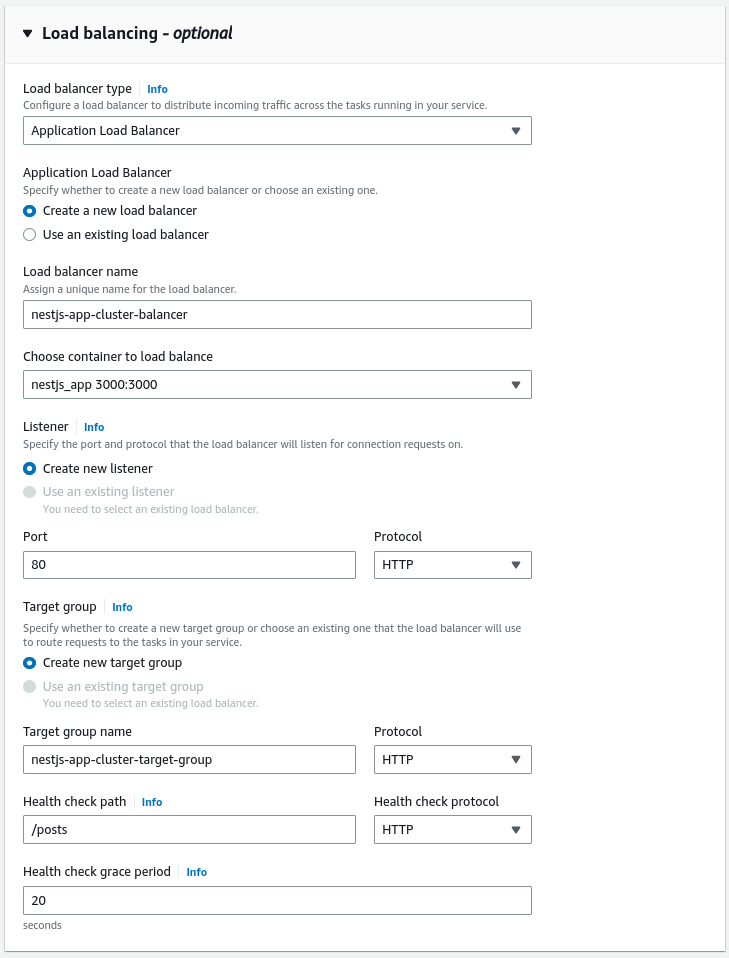
In AWS, target groups tell the load balancer where to direct the traffic. The load balancer periodically sends requests to the registered targets to test if they work as expected. These requests are called health checks.
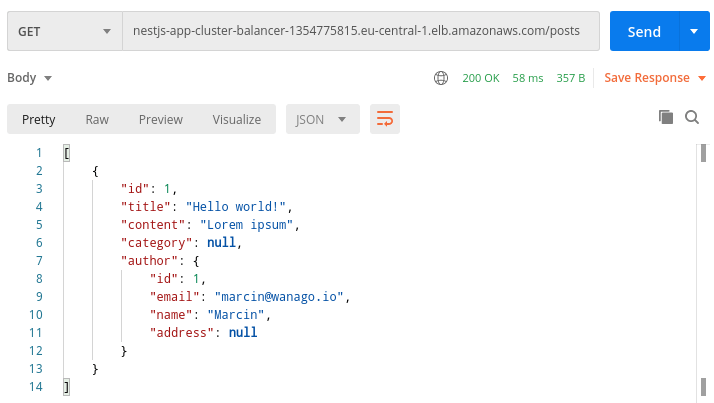
Our NestJS application has the /posts endpoint that returns the list of posts from the database. In this simple example, it can serve as a health check.
If you want to know more about health checks in general, check out API with NestJS #51. Health checks with Terminus and Datadog
Using the configured security groups
Running the above service causes two EC2 instances to be created. First, we need to open each of them in the EC2 user interface and modify their security configuration. Then, we need to add the security group we created at the beginning of this article.
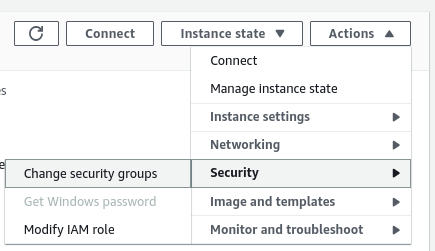
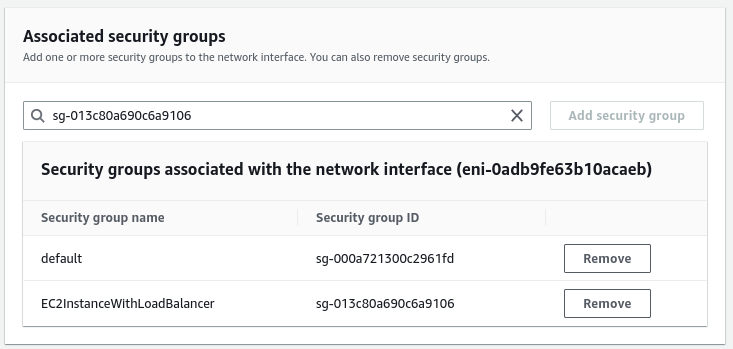
We must add the “EC2InstanceWithLoadBalancer” security group to both EC2 instances.
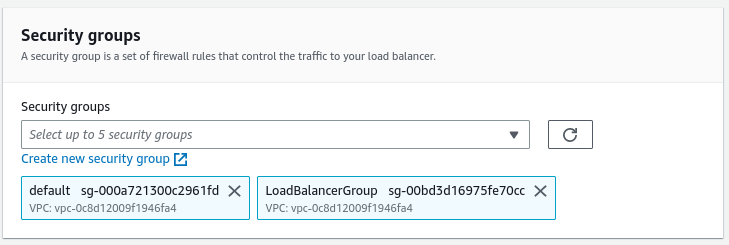
Now, we need to do a similar thing with our load balancer. We need to find our newly created load balancer on the list and modify its security configuration. This time, we need to add the “LoadBalancerGroup”.
Accessing our API
To find the URL of our API, we need to open the configuration page of our load balancer and look at the DNS name section.
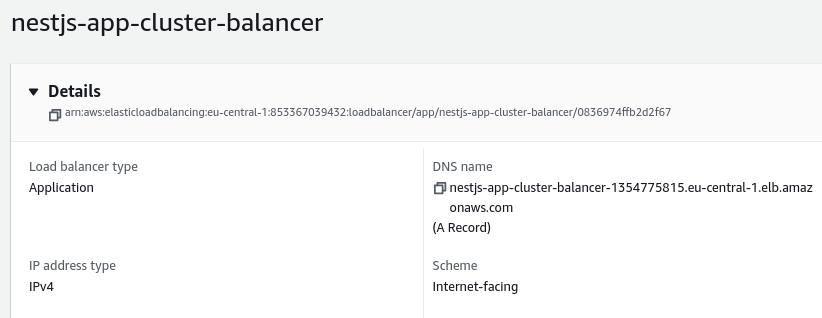
We can now use it to make requests to our API.
Summary
In this article, we’ve deployed multiple instances of our NestJS application through AWS. To distribute the traffic, we’ve used a load balancer. In addition, we configured new security groups for the load balancer to communicate with the EC2 instances.
Scaling our application horizontally using multiple instances of our application can help us deal with the incoming traffic. However, there are a few things to watch out for. We need to consider that the instances of our apps run independently of each other. For example, if we implement an in-memory cache, we end up with multiple instances of the cache and break the integrity of our data.
If you want to know more about in-memory cache with NestJS, check out API with NestJS #23. Implementing in-memory cache to increase the performance
To solve the above issue, we need to create a cache shared between multiple instances. A common solution is Redis. To get more information, read API with NestJS #24. Cache with Redis. Running the app in a Node.js cluster.
There is still more to learn about deploying NestJS with AWS, so stay tuned!
Hi Marcin, how about the situation when you have cron jobs etc? how do you ensure there is only 1 task of them running